What is CryptoLocker
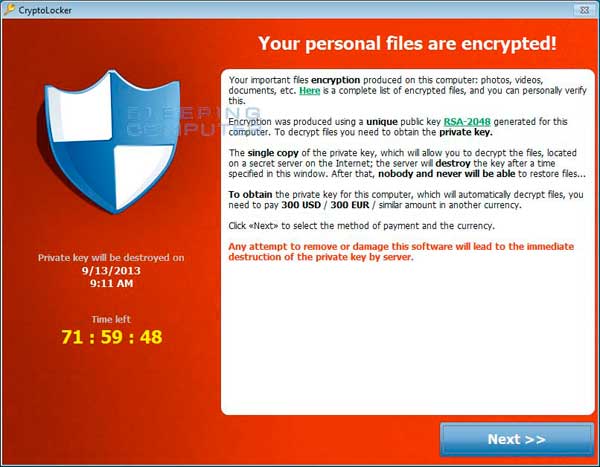
CryptoLocker is a ransomware program that was released around the beginning of September 2013. This ransomware will encrypt certain files using a mixture of RSA & AES encryption. When it has finished encrypting your files, it will display a CryptoLocker payment program that prompts you to send a ransom of either $100 or $300 in order to decrypt the files. This screen will also display a timer stating that you have 96 hours, or 4 days, to pay the ransom or it will delete your encryption key and you will not have any way to decrypt your files. This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program will decrypt the files that it encrypted
CryptoLocker will then begin to scan all physical or mapped network drives on your computer for files with the following extensions: *.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.pdf, *.eps, *.ai, *.indd, *.cdr, *.jpg, *.jpe, img_*.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c. When it finds a files that matches one of these types,it will encrypt the file using the public encryption key and add the full path to the file and the filename as a value under the
HKEY_CURRENT_USER\Software\CryptoLocker\Files Registry key.
When it has finished encrypting your data files it will then show the CryptoLocker screen as shown above and demand a ransom of either $100 or $300 dollars in order to decrypt your files. This ransom must be paid using Bitcoin or MoneyPak vouchers. It also states that you must pay this ransom within 96 hours or the private encryption key will be destroyed on the developer's servers.
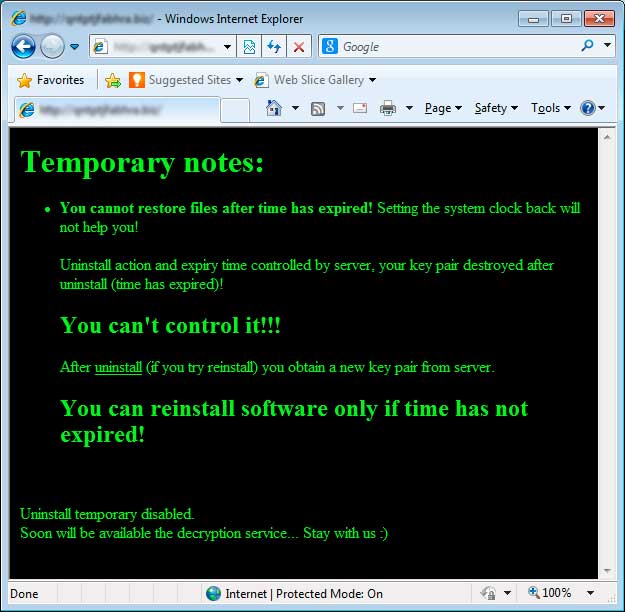 How to increase the time you have to pay the ransom
How to increase the time you have to pay the ransom
When the CryptoLocker is first shown, you will see a timer that states you need to pay the ransom within 96 hours. Some people have reported that you can increase the time by rolling back the clock in your BIOS. So to increase the timer by 10 hours, you would change your clock in your BIOS to 10 hours earlier. The virus author has
stated that using this method will not help. They have said that the private key required for decryption will be deleted from the Command & Control server after the allotted time regardless of how much time it says is left on the infected computer.

 for the last 10 years to protect customers and online transactions from threat. Over the time those remote attackers adapted to these countermeasures and sophisticated banking Trojans began to emerge.
for the last 10 years to protect customers and online transactions from threat. Over the time those remote attackers adapted to these countermeasures and sophisticated banking Trojans began to emerge.





